May 20, 2024
SECURITY COMPLIANCE AT CODE EXITOS
Safeguarding sensitive data isn't just a legal obligation but an ethical imperative.
Compliance frameworks are proven guidelines for ensuring our clients' and partners' trust and confidence. CODE Éxitos prioritizes security compliance and protects our organization, but it also upholds the trust placed in us by our clients and partners, ensuring their data remains safe and secure at all times.
SECURITY CERTIFICATIONS
Visit our Trust CenterVisit our Trust Center
Want to learn more about our progress and documentation of our compliance against global standards including certifications, attestations, and audit reports?
Request access to our Trust Center now:

SOC 2
ACTIVE
SOC 2 (Service Organization Control 2) serves as our guiding framework, defining rigorous criteria across key domains: security, availability, processing integrity, confidentiality, and privacy.

ISO 27001
LATE 2025
ISO 27001 is an information security management system (ISMS) that helps keep consumer data safe.

HIPAA
2025
HIPAA is a law requiring organizations that handle protected health information (PHI) to keep it protected and secure.

GDPR
2025
GDPR is a regulation in EU law on data protection and privacy in the European Union and the European Economic Area.
Our Auditors: Assurance Lab
As part of our security practices, the Assurance Lab team plays a vital role as our independent, third-party auditors. Assurance Lab meticulously scrutinizes every aspect of our processes, systems, and controls to provide an impartial and comprehensive assessment of our adherence to regulatory requirements and industry standards.

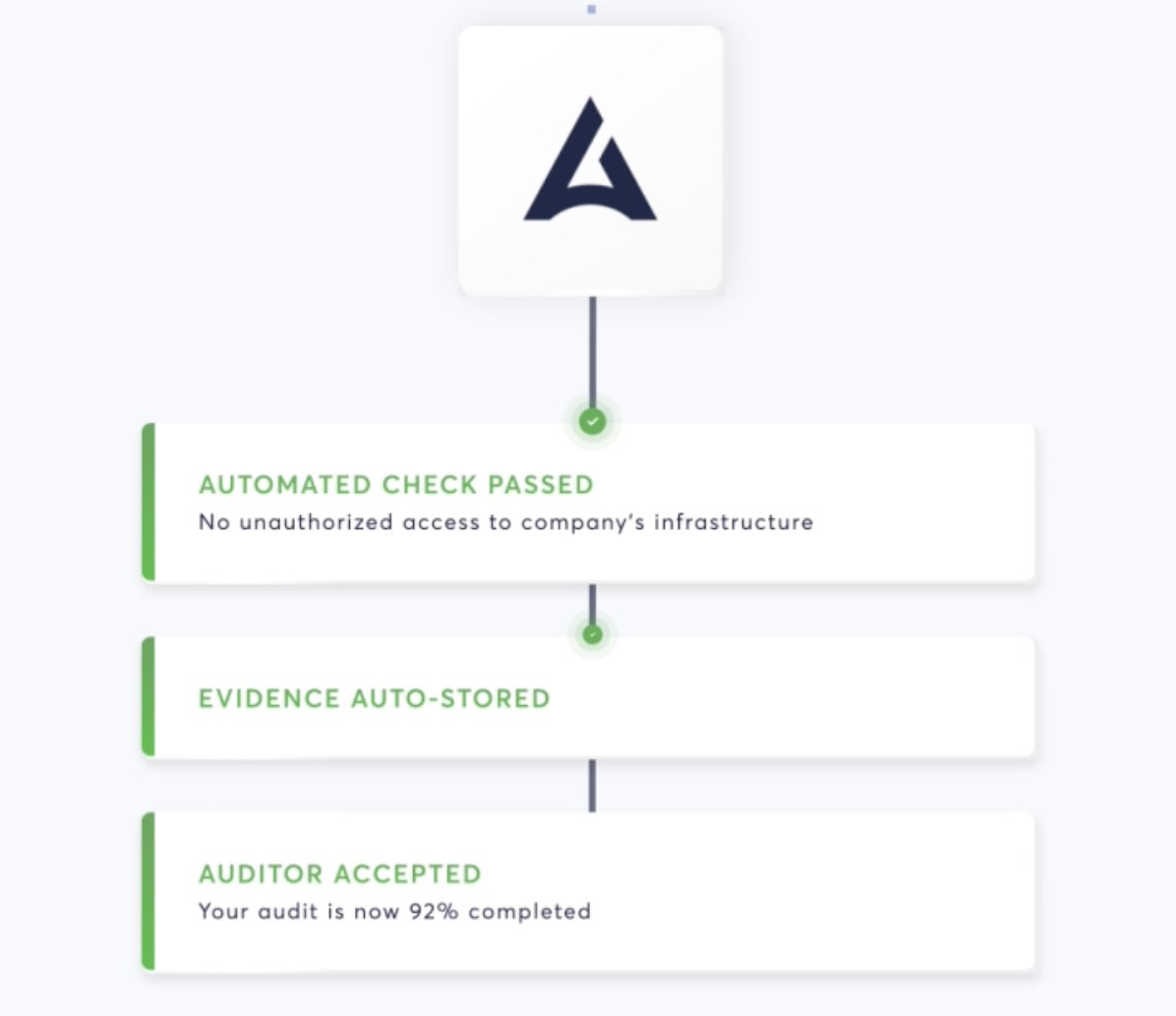
Continuous Security Control Monitoring
CODE Éxitos uses Drata’s automation platform to continuously monitor 55+ internal security controls across the organization against the highest possible standards. Automated alerts and evidence collection allow CODE Éxitos to confidently prove its security and compliance posture any day of the year while fostering a security-first mindset and culture of security compliance across the company.
Employee Trainings
Security is a company-wide endeavor. All CODE Éxitos employees complete an annual security training program and employ best practices when handling customer data. Throughout the year, we hold additional security workshops, discussions, and chats.
Secure Software Development
We employ a robust framework of manual and automatic data security and vulnerability checks throughout the software development lifecycle. This ensures that our software undergoes rigorous scrutiny to identify and address any potential vulnerabilities or security weaknesses at every step, from conception to deployment.

